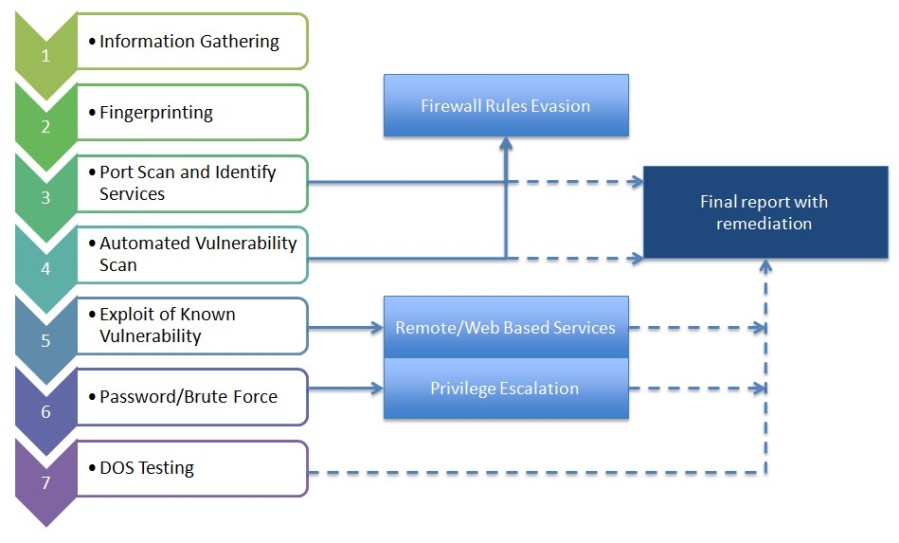
One of our key technology services, we use both freeware and commercial products to do PCI accepted penetration tests and vulnerability assessments. Our qualified personnel ensure that penetration testing methodologies such as Open Source Security Testing Manual Methodology (OSSTMM), Open Web Application Security Project (OWASP) and NIST 800-42/115 are being followed.
We have certified pentesters with peer-reviewed tools, and field experience, having done massive projects with more than 1,000 IPs in testing scope. Along with ASV vendors such as Control Case, we can coordinate and facilitate the ASV scans for PCI compliance projects, provided by ASV vendors.
Our international certifications are Certified Ethical Hacker (CEH) and Licensed Penetration Tester (LPT) from EC-Council (www.eccouncil.org), Certified Information Systems Security Professional (CISSP) from ISC2 (www.isc2.org), and GIAC Certified Penetration Tester (GPEN) from GIAC (www.giac.org).
An overview of our basic methodologies are as follows:
Web Application Penetration Test
Is your e-commerce site safe? Have your forms been set up properly? Are your users being validated? Is your code secure?
This exercise is focused on testing web application security. While the basic methodology is similar to other testing, there is additional focus on weaknesses unique to web applications, published by the Open Web Application Security Project (OWASP) group. The OWASP Top 10 Vulnerabilities that will be tested are:
A1 – Injection
A2 – Cross Site Scripting /XSS
A3 – Broken Authentication / Session Management
A4 – Insecure Direct Object References
A5 – Cross Site Request Forgery
A6 – Security Misconfiguration
A7 – Insecure Cryptographic Storage
A8 – Failure to Restrict URL Access
A9 – Insufficient Transport Layer Protection
A10 – Unvalidated Redirects and Forwards
Web Application testing, while mostly conducted against a public available website externally can also be done internally, if there are internal web applications deployed, for instance customised ERP solutions, or management systems that might contain sensitive data.
External and Internal Network Testing
Aside from application specific testing, we can also conduct tests against systems. For instance, in ensuring patches are updated, server weaknesses are addressed, network devices are secured etc.
Social Engineering testing
One of the social engineering test we do is to do ‘phishing’ exercises for enterprises. We simulate emails and dummy sites and track clicks on emails to see how many users actually click on a malicious link. In this way an enterprise will be able to tell how effective their human resource security and training initiatives are.
Call us at +603 6203 1888 or email us at avantedge@pkfmalaysia.com for more details of our Penetration Testing and Vulnerability assessment packages.
Leave a Reply