To all our readers and clients celebrating Chinese New Year,
May the good health, good luck and great success be with you always. For those who are travelling, wishing you a safe and peaceful journey!
After a relatively quiet 2012 on the penetration testing (PenTest) front, we’ve got quite a number of requests on our penetration testing services in the first month. A lot of clients we speak to don’t really have an idea of what a penetration testing exercise should be. Many of them expect us to do stress testing, load testing and basically all the scope that a QA/QC group should be doing for their software development. We do that as well, but that’s slightly different from a penetration test. Slightly here means, related, but with different objectives. Some pentest scope does have stress test elements, such as breaking the system with DDOS. In other words, the objective is to expose weaknesses and vulnerabilities, as well as to create exploitations, either through a conceptual or practical standpoint on these vulnerabilities.
The first thing to do is to define the objectives and scope. Most companies we’ve dealt with prefers a quick assessment to see immediate weaknesses. While there is nothing wrong with this, as pentesters, we must make our clients realise that this is simply a snapshot vulnerability and it’s not a catch-all. Scoping is usually done with a meeting with the business owners. IT infrastructure can be very large and complex. To pentest the entire infrastructure is obviously not practical, so we need to define a narrower scope based on risks and sensitivity of data. It’s a lot like our IT audits. We establish our audit universe and our incoming points, and then run our pentest exercise against it. Another scope is to establish the type of pentest. We’ve done pentest emulating disgruntled employee with authorised access looking to escalate privileges or remove data. We’ve simulated as script kiddies aiming for a take down on resources and DOS attacks. We’ve simulated concentrated attacks on a group of IP addresses, utilising OSSTMM methodology. Recently we just completed an OWASP Top Ten Web app penetration testing. We’ve had another where multiple attack vectors were looked into, such as HR weaknesses, process weaknesses and a vulnerable FTP server where other attacks can be launched from.
Mostly, the scope will be determined by cost and time. Due to the non-regulated world we live in, most companies won’t want to spend too much on a penetration testing exercise. This is unfortunate, because usually, only after we give our presentation of report, do people realise, “Man, we have all these problems??”
Another point is to define the rules of engagement. Unlike other engagements, penetration test is high risk. It’s controlled, but it’s still simulating an attack. In many apps we’ve tested, we’ve found that they have NEVER gone through any QA/QC testing in the first place. In one engagement, our benign scan brought down the whole HA cluster. Luckily, our Rules of Engagement was already in place, to do testing in a non-peak hour and had a standby team, and we brought back up the systems with no significant impact. Still, it highlights the criticality of treating the pentest exercise with utmost seriousness. We cannot determine how systems will react to our exercise 100%, but we can draw boundaries. For instance, in one project, we were only allowed to create a benign file to demonstrate compromised access. In another, we were permitted to put in a keylog software to demonstrate the ineffectiveness of both host controls and network controls. Most of all COMMUNICATION is the most important thing. We are not a bunch of dark-cloaked hackers out to destroy our client’s credibility. We inform our clients on progress daily, and in some instance, as we go through a critical exercise, step by step, through Skype of Gtalk. The client must feel secure and the only way is through properly diseminated information.
I spoke to a client before who had hired someone from the net to do a pentest. Not only was the pentest successful, but he suspects some data was even taken. Because there was no communication or rules of engagement, he couldn’t get a proper report out and because he did not know what has been compromised, he had to completely change his security passwords and such.
We’re not saying we’re the best in the world. We’re saying that in whatever we do, our best interest must be the client’s best interest. As a company, there is absolutely very little benefit in us destroying our reputation by doing a shoddy job or stealing information, and putting our business at risk.
If you want to know more about what we do, drop us a line at avantedge@pkfmalaysia.com and we will get one of our consultants to get back to you directly.
In the meantime, here’s to a great 2013 ahead to all!
Over the weekend, the team sat and brainstormed on some of the typical project situations and the impact arising, that makes project management so critical.
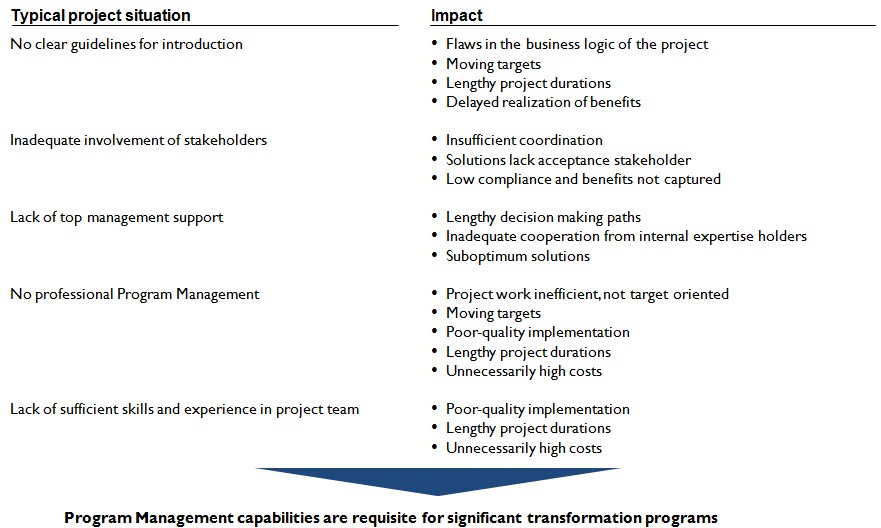
Efficient and responsible project management is key to any successful enterprise delivery. No matter how carefully planned a project is, without the competent supervision and coordination of all phases of the project implementation, a project is likely to become a headache.
The use of project management support techniques gives better initial planning and assessment risks by providing a greater chance of forecasting problem areas while there is time to take corrective action. This also allows flexibility for alternative modes of operation. The project management services offered by PKFAE concentrate on three prime issues of managing time, cost and resources.
PKFAE’s Project Management Philosophy behind every successful on-time project delivery follows these important aspects:
PKFAE has the experience to meet the challenges of any project management that a company is undertaking locally and nationwide. Some of the delivery services on offer include:
Whether you are embarking on a migration project, a system cleanup project or even an evaluation of new IT investment project; project management must be integral. It must provide an independent, non-biased, business side view of the efforts and report without partiality. It’s not to say that every project with project management becomes automatically a resounding success; but it’s better compared to projects without any management at all!
As a former head of IT security running close to 350 security devices worldwide for DHL, I think I have a pretty good grasp of problem solving skills. We used to deal with tens of incident tickets coming in. Tens of tickets might lead to fewer problems, but this doesn’t mean it gets easier. Problems might end up being just symptoms of a bigger issue. The list goes on. Having passed the ITIL cert, I was curious on how we could better manage problem resolution. Incident resolution I get it. Just get the service up and running either through a workaround or resolving the underlying problem. The former is what I now know as the ‘sweet spot’, distinct compromises that has an improvement and a worsening factor. The latter is problem management, which I haven’t done too well. Try having half of China yelling into your ear to get those F5 BigIP load balancers to work properly so that delivery planes are cleared to take off, or face a multi million of USD loss per hour.
I would venture to say all incidents should be dealt with to get the service up, but should also lead to a more methodical problem management, to solve the underlying issue so that it does NOT happen again.
Over the weekend, I attended an intriguing course by a reknowned practitioner of TRIZ, who worked with Intel.TRIZ is a russian acronym, and stands for Theory of Inventive Problem Solving. I hear some of you going, “Wait, that’s TIPS.” OK, TRIZ stands for teoriya resheniya izobretatelskikh zadatch, which in Russian, means “Don’t-try-to-pronounce-it-and-destroy-our-mother-tongue” to most of us. In fact the real writing is in russian script, which, to decipher it, would probably take me about the same time to be fluent in Middle-Earth Elvish.
But that aside, TRIZ is actually a very interesting way to look at problem resolution. It’s a concept supported by its own tools to look into a problem in an inventive manner. Meaning, we’re here to resolve contradictions. For instance, to solve my computer’s performance, I increase the CPU, but with that, I need to improve my cooling fan. That’s a contradiction. When something gets better, something else gets worse. Immediately, you’d think, why not spend extra money and buy a bigger cooling fan? Using TRIZ however, it does away with experiential learning and simply breaks down the function, understand the cause and effect, and trim away areas that are not relevant, until it comes up with a specific “Inventive Principle” to address the problem. In this case, it might just be putting the computer inside your data center with special external cooling, as opposed to under your desk, stacked with moldy papers.
One of the idea of TRIZ is to break down the problem into functions and identify worsening and improving parameters based on 39 Systems Parameters. Then, using the contradiction matrix, identify among the 40 Inventive Principles how to resolve these. The philosophy of the 40 principles is taken from thousands of patents, and how they address our needs. Apparently this is a conclusive list, and hasn’t changed since the 60s. That’s a pretty steady list.
After intensive training, we sat for the TRIZ certification exams and passed. So, PKF becomes the first management advisory firm with TRIZ certified people in it. A lot of it makes sense to me, as we always used to approach a problem in either a novel way or use our previous experience with the problem to address it. Both might or might not work, but with TRIZ, at least the alternatives are better mapped out.
Read it up in this WIKI, it’s quite an interesting concept; the world according to TRIZ!
Years ago, when I was starting out, I was given a book by my eventual father-in-law (though I didn’t know it at that time) called “Who Moved My Cheese?”. It’s a fascinating look at change management and pre-set my mind into what I am now in some respects: that change is Good. That change is Needed. That change should be Anticipated. I was a young rat then, entering into the race, and now a dozen years after reading that book, it still resonates somewhat in me. That change is great.
You can change a situation and not change a person. For instance, you might know someone who got retrenched. His situation changed. His cheese was taken away. But like some of the characters in the story, he sat down and mooned over his situation. Or you can change a situation and change a person. Someone else adapted to the situation and changed his mindset to address the new situation. Better yet, if you anticipate the change, and start moving before even your cheese is finished. The last part is certainly the hardest. This is mainly not due to our resistance to change, but to our comfort of the status quo.
Imagine we go to work everyday, with a set routine and do things from 9 to 6. When we’ve gone home, we spend time with family, watch our favourite show and crash for the night. Deep in our thoughts we have made up our mind to study a new system, or new language or develop a new methodology for IT risks, or even to diversify our income channels by going into investments. But we always say, well, not this day. And as the famous phrase from Scarlett O’Hara goes: “After all, tomorrow is another day.” The phrase of optimism and hope has turned the next generation into a generation of procrastinators, because ‘tomorrow’ is only a day away and we can do it tomorrow.
For an organisation such as ours, the inability to change is to die. The inability to anticipate is to be stagnant. The inability to innovate is to be left behind. The absence of evolution is the certainty of extinction. It might sound melodramatic, but it’s never so prominent in our case, in IT services.
We need to anticipate in two dimensions: The first is in the current product: the service, the input, the output of our sweat, our efforts, our WORK. How do we do the things we are doing better? How do we improve on the things we are currently selling? The second dimension is in the future ideas. I personally don’t believe in a Blue Ocean. I believe that whatever we do, there is no such thing as an impregnable barriers of entry. With that in mind, I do believe in not just doing things differently, but doing different things. Especially in IT, what are some of the future services we can anticipate? What happens when our IT audits and compliance cheese are finished? Which direction do we move in?
2013 will be in a lot of aspects a year of anticipated change. With more focus on security, we are looking at areas that previously has been ignored: the understanding of big data, the movement into mobility, the virtualisation of workspace.
Are we ready to move from our cheese station this year?
© 2025 PKF AvantEdge
— Up ↑